- ALL COMPUTER, ELECTRONICS AND MECHANICAL COURSES AVAILABLE…. PROJECT GUIDANCE SINCE 2004. FOR FURTHER DETAILS CALL 9443117328


Projects > COMPUTER > 2020 > NON IEEE > APPLICATION
Cloud computing is an Internet-based computing pattern through which shared resources are provided to devices on demand. Its an emerging but promising paradigm to integrating mobile devices into cloud computing, and the integration performs in the cloud based hierarchical multi-user data-shared environment. With integrating into cloud computing, security issues such as data confidentiality and user authority may arise in the mobile cloud computing system, and it is concerned as the main constraints to the developments of mobile cloud computing. In order to provide safe and secure operation, a hierarchical access control method using modified hierarchical attribute-based encryption (M-HABE) and a modified three-layer structure is proposed in this project. In a specific mobile cloud computing model, enormous data which may be from all kinds of mobile devices, such as smart phones, functioned phones and PDAs and so on can be controlled and monitored by the system, and the data can be sensitive to unauthorized third party and constraint to legal users as well. The novel scheme mainly focuses on the data processing, storing and accessing, which is designed to ensure the users with legal authorities to get corresponding classified data and to restrict illegal users and unauthorized legal users get access to the data, which makes it extremely suitable for the mobile cloud computing paradigms.
In the existing system, fuzzy Identity-Based Encryption (IBE) was used as the prototype of ABE. Latterly, a variant of ABE named CP-ABE was proposed. Since Gentry and Silverberg proposed the first notion of hierarchical encryption scheme, many hierarchical CP-ABE schemes have been proposed. For example, Wang et pl. proposed a hierarchical ABE scheme by combining the hierarchical IBE and CP-ABE. Wan et al. proposed hierarchical ABE scheme. Later, Zhou gave a hierarchical ABE scheme, while the length of secret key is linear with the order of the attribute set. A cipher text policy hierarchical ABE scheme with short cipher text is also studied. In these schemes, the parent authorization domain governs its child authorization domains and a top-level authorization domain creates secret key of the next-level domain. The work of key creation is distributed on multiple authorization domains and the burden of key authority centre is lightened.
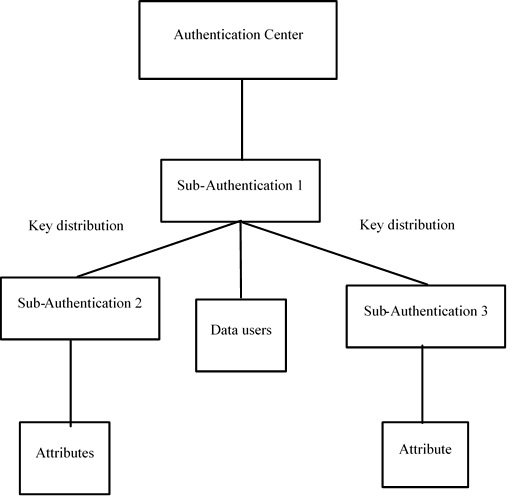
The current method M-HABE is being designed such that it overcome all the issues that are being faced by the people with the existed methods such as Cipher text-policy ABE, Hierarchical identity based encryption, CMA approach, etc. In this paper, a hierarchical access control method using a modified hierarchical attribute-based encryption (M-HABE) and a modified three layer structure is proposed. A modified hierarchical attribute based encryption (M-HABE) access control method applied in mobile cloud computing is proposed in this paper , which changes a proposed scheme called hierarchical attribute-based encryption HABE, M-HABE combines the hierarchical identity based encryption(HIBE) and the cipher text policy-attribute based encryption (CPABE). In the authentication centre the keys should have the same identical hierarchical structure as users privilege levels structure has. Based on all these aspects, a modified hierarchical attribute-based encryption (MHABE) have been proposed in this research and further this access control method is applied in mobile cloud computing. This proposed method is the advanced scheme of HABE (Hierarchical Attribute-Based Encryption) In this project, with the development of e-commerce, a growing number of customers choose to go shopping online because it saves time and effort. However, it always contraries to expectations of customers. This is because they may need to pick up one choice among thousands of products. To help customers identify attractive products, a skyline query is admittedly a common and effective methodology. According to the definition of the skyline query, a product which is not dominated by any other product is said to be a skyline product or it is in the skyline. The products in the skyline are the best possible trade-offs between all the factors that customers care about. The skyline query is useful in identifying attractive products.
Architecture Diagram